Pam Byse Parents - Digital Oversight And Protection
In a world that feels more connected than ever, keeping things safe, especially our digital bits and pieces, has become a very big deal. It's almost like thinking about who looks after the important stuff, who makes sure everything is in its proper place and that no one gets into areas they shouldn't. This idea of watchful care and careful handling is, you know, a lot like what we think of when we consider protective figures in our lives.
So, when we talk about something called "Privileged Access Management," or PAM for short, it's actually about creating a sort of digital safety net. It's about setting up clever ways and smart tools to really keep an eye on who can get to the most sensitive parts of our digital systems. Think of it as having a very clear set of rules for who holds the keys to the most important rooms in a house, or perhaps, who gets to decide what happens with truly valuable family heirlooms. It’s a pretty important concept, really.
This whole idea, in a way, aims to bring a sense of order and security to the sometimes chaotic digital landscape. It’s about making sure that those with special access, like system administrators or folks dealing with sensitive information, use their capabilities responsibly. Just like good parents might set boundaries and provide guidance, PAM tries to do that for digital permissions, ensuring that everything runs smoothly and securely, which is rather comforting to know, isn't it?
Table of Contents
- What is Privileged Access Management (PAM)?
- How Does PAM Act Like Pam Byse Parents for Your Data?
- The Role of PAM in Safeguarding Sensitive Information
- Why is PAM Important for Modern Organizations?
- Oncor's Approach to Operational Security
- How Does Oncor Manage Its Digital Environment?
- The Human Element - Protecting Accounts and Activities
- Can PAM Truly Be Your Digital Pam Byse Parents?
What is Privileged Access Management (PAM)?
Privileged Access Management, or PAM, is a kind of cybersecurity plan and set of tools that helps keep a very tight grip on who has special permissions in computer systems. It's about making sure that people, or even just automated programs, who have what we call "elevated" access – meaning they can do more than a typical user – are properly controlled. This control means watching what they do, making sure they follow rules, and keeping their access safe from those who might want to misuse it. It's a pretty important piece of the puzzle when you're trying to keep digital information secure, actually.
PAM - A Protective Framework for Digital Assets
So, in some respects, PAM works like a protective framework for all the valuable digital things an organization has. It's like having a very thorough security guard for the most important parts of a building. This system helps keep an eye on all identities across an IT environment, making sure that every single person or program that touches the network is accounted for and that their actions are known. It’s a way of making sure that only the right people can do the right things with sensitive information, which is a big deal for keeping everything safe and sound, you know.
How Does PAM Act Like Pam Byse Parents for Your Data?
You might wonder, how does this technical thing, PAM, relate to something as personal as "pam byse parents"? Well, in a metaphorical way, PAM acts a lot like a very watchful and caring guardian for your digital information. Just like parents often set boundaries and provide a safe environment for their children to grow, PAM creates a secure space for your data. It defines who gets to do what, when, and how, making sure that sensitive information isn't exposed to unnecessary risks. It's about providing a kind of digital upbringing for your data, really, guiding its interactions and protecting it from harm.
Keeping a Watchful Eye on Digital Identities
This means that PAM is constantly keeping a watchful eye on every digital identity within a system. It's not just about stopping bad guys; it's also about making sure that even the good guys, those with special access, are using their privileges correctly. It's like a parent who teaches their child how to use tools safely and responsibly. PAM ensures that privileged accounts, like those used by system administrators, are not misused, whether accidentally or on purpose. This kind of oversight is pretty essential for maintaining a healthy and secure digital environment, and it’s a bit like providing constant guidance and supervision, too.
The Role of PAM in Safeguarding Sensitive Information
The core purpose of PAM is to safeguard sensitive information. This includes everything from customer details to financial records and even the very code that makes systems run. It’s about making sure that only authorized individuals can access and work with this kind of data. This is a branch of cybersecurity that really focuses on protecting those special accounts that have a lot of power. It's like putting the most valuable family jewels in a very secure vault, and only a select few have the combination, you know?
Understanding the "Elevated" Access Points
To really get how PAM works, it helps to understand what "elevated access" means. These are the permissions that allow someone to make big changes to a system, access highly confidential information, or control critical operations. PAM focuses on these specific points because they are the most attractive targets for anyone trying to cause trouble. It’s a bit like knowing which doors in a house lead to the most important rooms and then making sure those doors have the strongest locks and are constantly monitored. This careful attention to these key access points is what makes PAM such a vital part of keeping things secure, honestly.
Why is PAM Important for Modern Organizations?
For any organization operating today, PAM is simply not an optional extra; it's a fundamental necessity. With digital threats growing more sophisticated every day, having a robust system to manage privileged access is critical for protecting against data breaches, insider threats, and regulatory compliance failures. It's like building a very strong foundation for a house; without it, the whole structure is vulnerable. This makes PAM a cornerstone of a good cybersecurity posture, and it's something every business, big or small, really needs to consider seriously.
Protecting Against Digital Intruders
PAM helps protect against digital intruders by making it incredibly difficult for unauthorized individuals to gain control of critical systems. Even if an attacker manages to get past initial defenses, PAM acts as another layer of security, limiting their ability to move around freely and access valuable information. It’s like having multiple checkpoints within a secure facility, making sure that even if someone gets through one, they'll face another barrier. This layered approach is pretty effective at keeping the bad guys out and ensuring that sensitive data stays where it belongs, which is a very good thing, you know.
Oncor's Approach to Operational Security
Moving from the general concept of PAM, let's look at a real-world example of an organization that takes security seriously, like Oncor Electric Delivery. Oncor, a major energy provider, deals with massive amounts of critical infrastructure and customer data. Their operational security is paramount, not just for their business, but for the millions of people who rely on their services. They have personnel, like those involved in damage assessment and power restoration, who need privileged access to sensitive systems to do their jobs effectively, especially after something like a winter storm. So, their approach to security is quite comprehensive, you know.
Powering Communities, Protecting Information
Oncor is all about powering communities, but they also understand that protecting information is just as vital. They use various systems to manage their operations, from monitoring power outages to managing customer accounts. This means they have to be incredibly careful about who has access to these systems and what they can do. It's not just about keeping the lights on; it's also about keeping customer data safe and ensuring the integrity of their network. Their dedication to security is pretty clear, as they work to restore power quickly and safely while also protecting sensitive operational details, which is actually a big job.
How Does Oncor Manage Its Digital Environment?
Oncor manages its digital environment through a combination of robust systems and careful procedures. They have processes for everything from signing into accounts securely to receiving alerts about power outages. This involves a lot of behind-the-scenes work, like managing user access and ensuring that only authorized personnel can make changes or access sensitive information. It’s a very complex operation, really, making sure that millions of residents receive energy reliably while also keeping their vast digital infrastructure safe from harm. They have to be very, very organized.
Ensuring Continuous Service and Data Safety
A big part of Oncor's strategy involves ensuring continuous service and data safety. They leverage things like weather monitoring systems to keep communities informed about potentially dangerous conditions, which shows their proactive stance. This kind of foresight and preparedness extends to their cybersecurity practices as well. They understand that protecting their systems is directly linked to their ability to provide uninterrupted service. So, whether it's managing account sign-ins or responding to a storm, their focus is on both operational efficiency and maintaining a secure digital environment, which is a pretty demanding task.
The Human Element - Protecting Accounts and Activities
Even with the most advanced technology, the human element is always a key part of security. PAM isn't just about software; it's also about defining roles and responsibilities for people. These roles are often set up manually, making sure that each person only has the access they absolutely need to do their job, and nothing more. This principle, known as "least privilege," is a very important part of keeping things secure. It's like giving someone only the specific tools they need for a task, rather than handing them the entire toolbox, you know?
User Roles and Defined Responsibilities
In a system protected by PAM, every user role has clearly defined responsibilities and corresponding access levels. This means that an administrator account, which has wide-ranging capabilities, is treated with the highest level of scrutiny and protection. It's about making sure that every action taken by a privileged account is logged, monitored, and audited. This helps to catch any unusual activity quickly and prevent potential misuse. It's a bit like having a clear job description for every digital role, making sure everyone knows their place and what they are allowed to do, which actually helps keep everything running smoothly.
Can PAM Truly Be Your Digital Pam Byse Parents?
So, can Privileged Access Management truly be thought of as your digital "pam byse parents"? In a way, yes, it can. While it's a technical system, the underlying principles are quite similar to the protective, guiding role that parents often play. PAM looks after your most valuable digital assets, sets boundaries for access, monitors behavior, and works to prevent harm. It provides a framework of care and control that ensures the safety and well-being of your digital environment. It's a powerful tool for guardianship in the digital world, making sure that what's important stays safe and sound, which is really what you want, isn't it?
A Metaphor for Comprehensive Digital Care
This metaphor of "pam byse parents" for PAM highlights its role in providing comprehensive digital care. It’s not just about locking things down, but about intelligent oversight, continuous monitoring, and proactive protection. Just as parents strive to create a secure and nurturing environment, PAM aims to build a robust and resilient digital space where sensitive information can exist and be used safely. It’s a very important piece of the modern security puzzle, ensuring that your digital family, so to speak, is well-protected and cared for, which is a rather comforting thought.
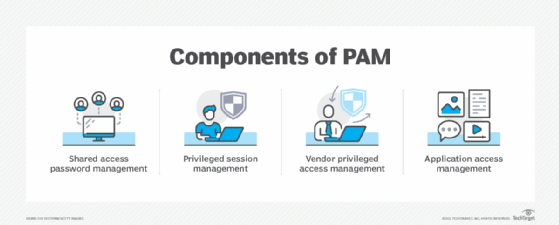
What is privileged access management (PAM)? (2022)
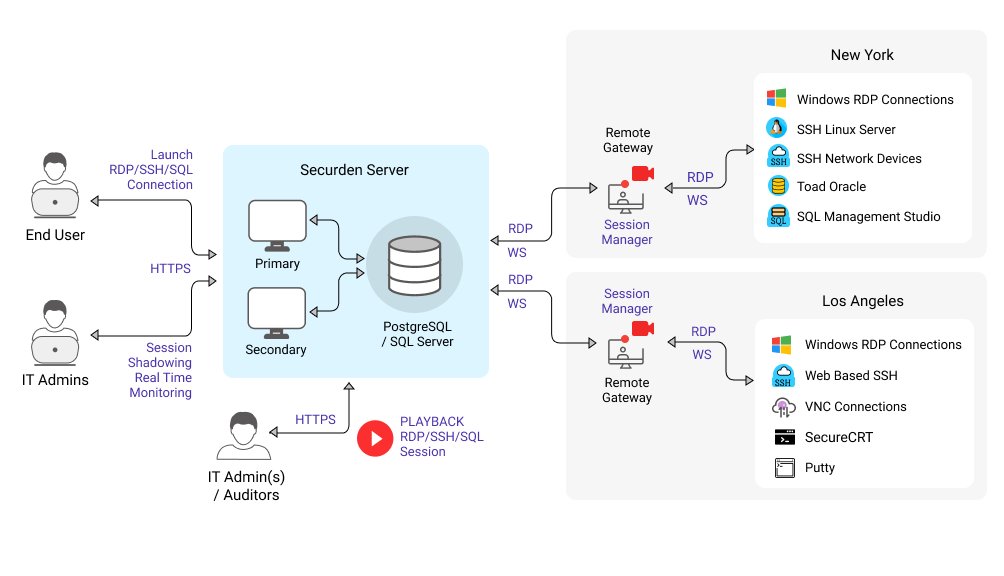
What Is A Pam Site at Robert Fabry blog
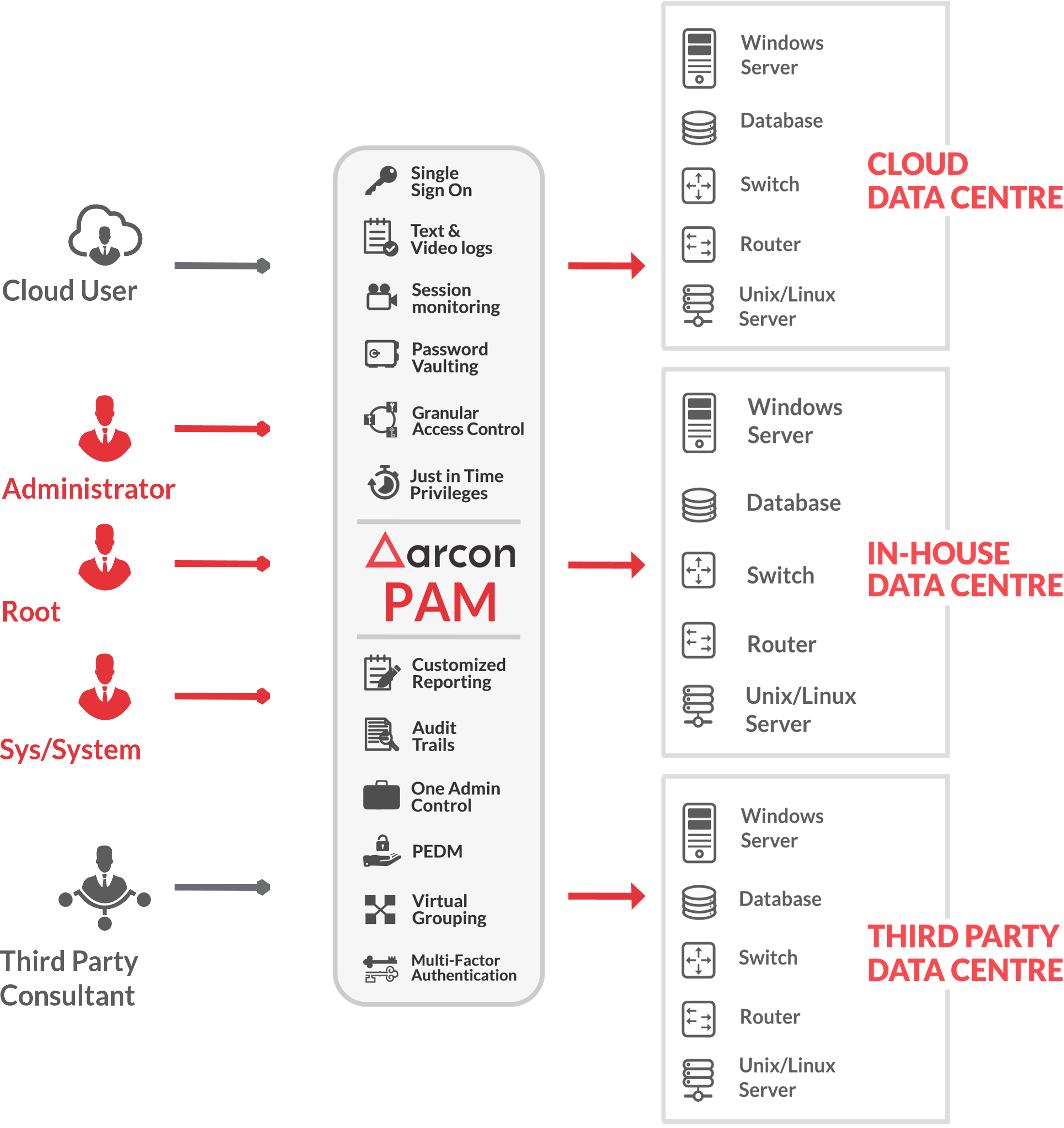
ARCON - лидер Gartner в PAM (Privileged Access Management)