Securely Connect Remote IoT To AWS VPC - A Simple Guide
Getting your little smart gadgets out in the world to talk with your central computer systems can feel a bit like a puzzle, especially when you want everything to be truly safe and sound. These devices, often far away, might be collecting all sorts of information, from the temperature in a remote warehouse to the status of a faraway machine. You want those far-off machines, the ones gathering information from all sorts of places, to send their data back home without any trouble. This is about making sure that connection is private, like a secret handshake, and that no one can peek at what's being sent or mess with it. We will talk about how to make those distant Internet of Things devices talk directly and safely with your private cloud network on Amazon Web Services, keeping your information locked up tight and out of sight.
Table of Contents
- What Makes Remote IoT Connections Tricky?
- How Does a Private Cloud Network Help?
- What Are the Main Ways to Connect?
- Is Your Remote IoT Setup Really Safe?
- What About Identity and Access?
- How Can We Monitor Our Secure Remote IoT Connections?
- What Happens If Something Goes Wrong?
- Putting It All Together for Remote IoT
What Makes Remote IoT Connections Tricky?
Connecting little Internet-connected things that are far away to a central system can sometimes feel like trying to send a message across a very busy street. There are quite a few things that make this a bit more involved than just plugging something in. For one, these devices are often out in the open, perhaps in places without much physical protection. This means someone could potentially get their hands on them, so you need to think about how to keep the device itself safe, you know, physically.
Then there's the question of how they actually talk to the main computer setup. They might be using public internet pathways, which are sort of like open roads where anyone can see who's driving by. This means the information they send could be seen by others if you are not careful. So, a big part of the puzzle is making sure those messages are private and that no one can easily listen in or change what's being said. It's about keeping secrets secret, as a matter of fact.
Another thing is that these little gadgets often have limited resources. They might not have a lot of computer power or battery life, which means you cannot always put super heavy-duty security features right onto the device itself. You have to be smart about how you protect them, using methods that do not drain their power or slow them down too much. This requires a bit of clever thinking, really, to get it just right.
Also, these devices might be sending data all the time, or just every now and then. The way they send information, and how often, affects how you should protect it. It is not a one-size-fits-all situation. You need a system that can handle lots of different kinds of little gadgets and their unique ways of communicating. This is where a bit of planning comes in, obviously.
Keeping Remote IoT Data Securely Sent
When you want to securely connect remote IoT devices, the goal is to make sure their messages travel safely from wherever they are to your private cloud space. This means creating a kind of private tunnel for the information. Think of it like building a special, protected lane on that busy street, just for your data. This lane ensures that only your data can travel there, and it is shielded from curious eyes or anyone trying to mess with it.
One way to do this is to make sure the devices can prove who they are before they even start talking. This is like having a secret password or a special ID card. If a device cannot show its proper ID, then it simply cannot join the conversation. This step is super important for keeping unwanted guests out of your system, so you know, it is a good first line of defense.
The messages themselves also need to be scrambled up before they leave the device. This is called encryption, and it turns the data into gibberish that only your central system can unscramble. Even if someone were to somehow peek at the message while it is traveling, they would just see a jumble of letters and numbers that makes no sense. This is a very good way to keep your information private, basically.
Setting up these secure pathways means thinking about a few things. You need to pick the right tools and methods that fit your specific devices and how they need to talk. It is not just about putting one lock on the door; it is about putting several locks and making sure they all work together. This helps ensure that your remote IoT data is always securely sent, from start to finish, which is quite important.
How Does a Private Cloud Network Help?
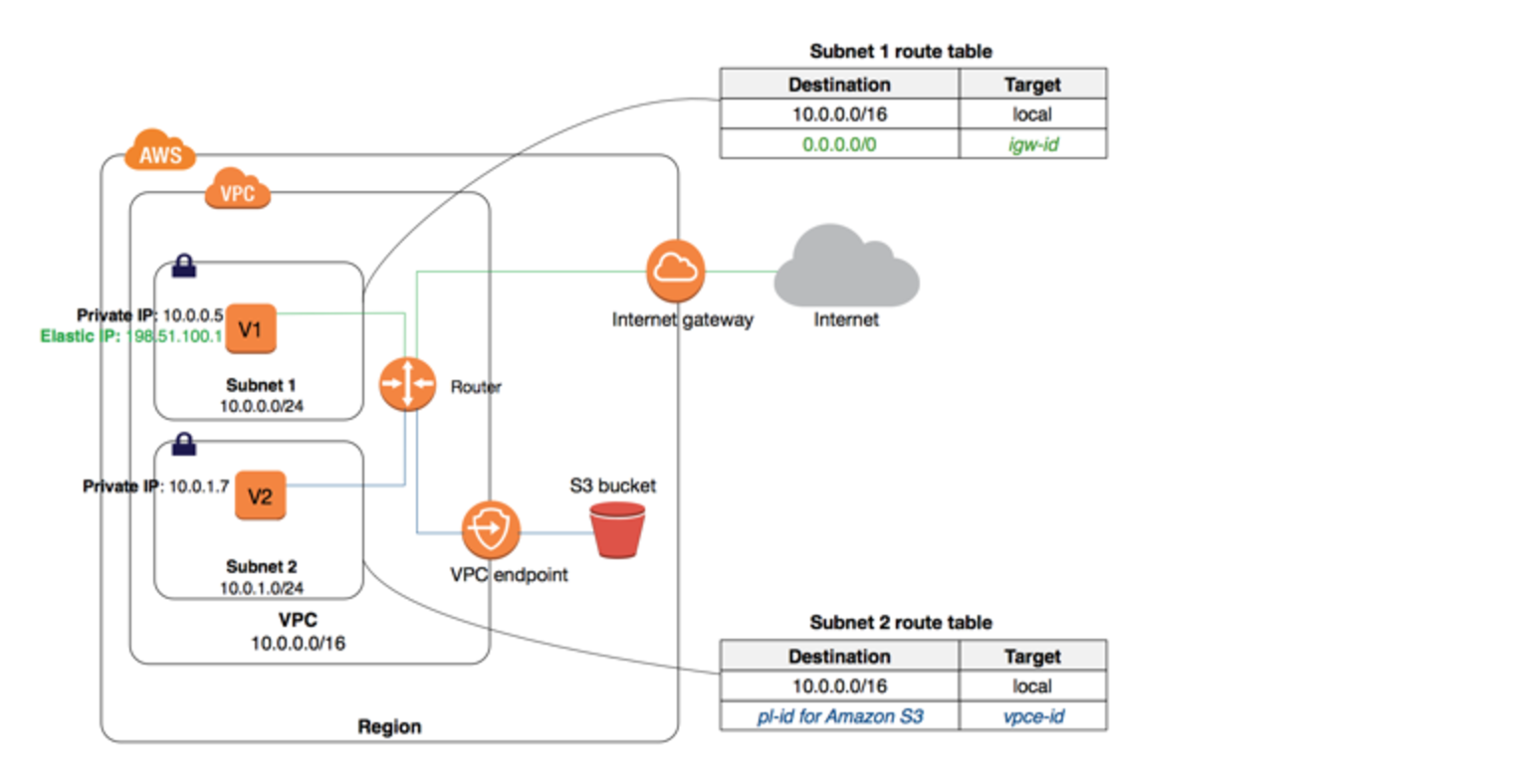
A private cloud network, often called a Virtual Private Cloud or VPC, is a lot like having your own special, fenced-off area within a much bigger public park. In this case, the park is Amazon Web Services, and your fenced-off area is where all your own computer servers and data live. It gives you a place that is just for your stuff, separate from everyone else's. You get to decide who comes in and who goes out, which is a pretty big deal.
When your remote devices want to talk to your main computer systems, having them connect into your own private area in the cloud means they are not just shouting their messages out into the general internet. Instead, they are sending them directly into your protected space. This significantly cuts down on the chances of someone else intercepting or interfering with the messages, you know, because it is a private road.
Within this private cloud space, you have a lot of control over how things are set up. You can put up virtual walls, decide which specific computer programs can talk to each other, and even control the flow of information down to very fine details. This level of control is really helpful for making sure that only authorized devices and systems can communicate, and that they do so in a way you approve. It is like being the boss of your own digital neighborhood, in a way.
This kind of setup also means you can keep your sensitive information and applications away from the public eye. Your data stays within your own controlled environment, which is a big plus for security. It provides a kind of safe haven for your operations, which is quite comforting when you are dealing with important information, obviously.
Why a VPC for AWS Remote IoT Connections?
Using a VPC for your AWS remote IoT connections gives you a dedicated, isolated space within the larger Amazon Web Services system. This isolation is a key benefit. It means your little devices are not just connecting to a general public internet spot, but rather to a specific, private part of the cloud that you control. This makes it much harder for outsiders to even find your systems, let alone try to get into them. It's almost like having an unlisted phone number for your critical systems, you know.
Within your VPC, you can set up very specific rules about what can talk to what. You can say, for example, that only your IoT devices can talk to a certain data collection program, and that program can only talk to a specific database. This kind of fine-tuned control helps prevent problems from spreading if one part of your system were to have an issue. It creates clear boundaries, which is pretty useful.
A VPC also lets you use other AWS services that are built for security, but in a way that is integrated with your private network. You can add things like special firewalls that check every piece of information coming in and out, or systems that automatically watch for strange activity. These tools work together to give you a very strong defense around your remote IoT setup. It helps keep everything buttoned up tight, really.
When you are looking to securely connect remote IoT devices, a VPC provides the groundwork for a solid security plan. It is the digital equivalent of building a strong foundation for a house. Without it, everything else you try to do for security might not be as effective. It gives you that private, controlled environment where you can truly manage who talks to your devices and what they say, which is a big deal, actually.
What Are the Main Ways to Connect?
When it comes to getting your far-off little gadgets talking to your central systems, there are a few main paths you can take. Each path has its own way of working and its own set of things to consider. The choice often depends on how much data your devices need to send, how quickly they need to send it, and how important it is that the connection stays absolutely private. It's a bit like choosing the right road for a trip, you know.
One common way is to use something called a VPN, which stands for Virtual Private Network. This creates a secure, encrypted tunnel over the public internet. Think of it like putting your car inside a special, armored transport vehicle that travels on the regular highway. The information inside is protected, even though the outer vehicle is on a public road. This is a pretty popular choice for many, as a matter of fact.
Another option involves using dedicated lines or special connections directly from your physical location to Amazon Web Services. This is like building your very own private highway straight to the cloud. It offers very high speed and a very consistent connection, and it is separate from the public internet entirely. This is often used for very important systems that need top-tier performance and privacy, you know, for the big stuff.
Sometimes, for smaller devices or those that do not send a lot of data, you might use a more direct approach through an IoT service that manages the connections for you. These services often have built-in ways to handle the security and identity of the devices. They act as a kind of middleman, making sure the messages get from the device to your private cloud space in a safe manner. This can simplify things quite a bit, apparently.
Direct Links for Securely Connecting Remote IoT
For some situations, having a very direct and private link is the best way to securely connect remote IoT devices. These direct links are not just using the regular internet; they are more like a dedicated telephone line straight to your cloud setup. One common way to do this is through something like AWS Direct Connect. This literally creates a physical network connection from your data center or office directly to an AWS location.
When you have a Direct Connect link, your remote IoT devices can send their information over this private line. It means the data never touches the public internet, which adds a very strong layer of privacy and security. It is like having your own private delivery service for your information, rather than relying on the public postal system. This can be quite reassuring, really.
Another type of direct link can involve setting up specific virtual private gateways within your AWS VPC. These gateways allow your remote sites or devices to establish secure tunnels directly into your private cloud network. Even if the data has to travel over the internet for a short distance, these tunnels ensure that the information is scrambled and protected the entire way. It is a bit like putting your secret message inside a locked box before sending it, you know.
Choosing direct links for securely connecting remote IoT can give you better control over network performance and can help meet very strict security requirements. It reduces the number of points where something could go wrong or where someone could try to interfere with your data. For operations where every bit of data integrity and privacy matters, these direct approaches are often the preferred way to go, so, it is worth looking into.
Is Your Remote IoT Setup Really Safe?
Once you have your remote devices talking to your cloud system, a big question always remains: is it truly safe? It is not enough to just set up a connection; you need to constantly check and make sure that no one is trying to get in or that no weaknesses have appeared. Think of it like keeping your house secure; you do not just lock the doors once and forget about it. You check them regularly, you know.
Part of making sure your remote IoT setup is safe involves regularly looking for weak spots. This could mean checking the software on your devices, making sure it is up to date and that there are no known problems. It also means reviewing the rules you have set up for who can talk to what, to make sure they are still appropriate and tight. This is a continuous process, actually.
Another piece of the safety puzzle is having systems that watch for unusual activity. If a device suddenly starts sending a huge amount of data, or if it tries to connect from a strange location, you want to know about it right away. These kinds of alerts can help you catch problems before they become big issues. It is like having a good alarm system that tells you if something is amiss, obviously.
And then there is the human element. Making sure that the people who manage these systems understand how to keep them safe is also very important. Training and clear guidelines help everyone do their part in maintaining a secure environment. Because, at the end of the day, even the best technology needs good people to run it, really.
Best Steps to Securely Connect Remote IoT to AWS
To securely connect remote IoT devices to AWS, there are several key steps you should put into place. First off, make sure every single device has its own unique identity, like a special badge. This means using things like digital certificates or unique keys so that only your approved devices can talk to your system. This is a very fundamental security measure, you know, like giving everyone a distinct fingerprint.
Next, always make sure the messages sent between your devices and AWS are scrambled up. This is called encryption, and it keeps your data private even if someone manages to intercept it. It is like putting your important letter in a code that only the intended recipient can read. This is pretty standard practice for anything sensitive, as a matter of fact.
Also, use the principle of "least privilege." This means giving your devices and the programs they interact with only the bare minimum permissions they need to do their job, and nothing more. If a device only needs to send temperature readings, it should not have the ability to, say, delete files. This limits the damage if something goes wrong with a device, which is quite sensible.
Set up good network boundaries within your AWS VPC. Use things like security groups and network access control lists to control exactly which parts of your system can talk to each other and from where. This creates virtual fences and gates around your different components, making it much harder for unauthorized traffic to move around. It is a very effective way to contain potential issues, really.
Finally, keep everything updated. Software on your devices, on your cloud systems, and all the security tools should be regularly checked for new versions and security patches. Old software can have known weaknesses that attackers might try to use. Staying current is a simple but very effective way to keep your remote IoT connections safe. It is just good practice, obviously.
What About Identity and Access?
When we talk about identity and access for your remote IoT setup, we are really talking about who gets to do what, and how we know they are who they say they are. It is like a very strict bouncer at the door of a private club. Every device, every person, and every program that wants to interact with your system needs to show its credentials first. This is a foundational piece of keeping things safe, you know.
For your little IoT gadgets, this often means giving them a unique digital certificate. This certificate is like a passport that proves the device is legitimate and belongs to your fleet. When the device tries to connect, it presents this certificate, and your AWS system checks if it is valid. If it checks out, the device is allowed to proceed; if not, it is turned away. This is a very clear way to manage who is allowed in, basically.
Beyond just letting devices connect, you also need to control what they can actually do once they are connected. A device that measures light levels probably does not need permission to turn off a factory machine. So, you set up very specific rules that define what each device or program is allowed to read, write, or execute. This prevents a compromised device from causing wider problems. It is a bit like giving someone a key only to the rooms they need to enter, not the whole building, really.
Amazon Web Services has tools like AWS IoT Core that help manage these identities and access rules for your remote IoT devices. These tools make it easier to give each device its own set of permissions and to revoke those permissions if a device is lost or stolen. It streamlines the process of keeping track of all your connected things and what they are permitted to do, which is pretty handy, as a matter of fact.
How Can We Monitor Our Secure Remote IoT Connections?
Once you have gone through all the effort to securely connect remote IoT devices, you really need a way to watch over them. Monitoring is like having a security guard who is always on duty, keeping an eye on everything that is happening. You want to know if a device stops sending data, if it starts sending strange data, or if someone is trying to get into your system without permission. This watchful eye is super important for ongoing safety, you know.
One way to monitor is to collect logs, which are like detailed diaries of everything that happens. Every time a device connects, sends data, or tries to do something, it gets written down. By looking through these diaries, you can spot unusual patterns or signs of trouble. These logs can be stored in services like Amazon CloudWatch or Amazon S3, making them easy to review later. It gives you a clear record of events, basically.
You can also set up alarms or alerts. If certain conditions are met – for example, if a device tries to connect from an unknown location, or if too many failed login attempts happen – an alarm can go off. This can send you a message, an email, or even trigger an automatic action to investigate or block the suspicious activity. This proactive approach helps you react quickly to potential issues, which is quite helpful, actually.
Tools within AWS, like AWS IoT Device Defender, are specifically made to help you monitor your IoT fleet. They can check your device configurations against best practices, detect unusual behavior, and even help you manage security updates. Using these specialized tools makes the job of watching over your secure remote IoT connections much simpler and more effective. It is like having a dedicated expert on your side, really.
What Happens If Something Goes Wrong?
Even with the best plans to securely connect remote IoT devices, sometimes things can go wrong. A device might get lost, someone might try to break in, or a software problem could pop up. When these things happen, having a plan for what to do next is just as important as having a plan for setting things up. It is like having an emergency kit ready, just in case, you know.
One key part of this is being able to quickly stop a device from communicating if it seems to be compromised. If a device is stolen or starts acting strangely, you need to be able to revoke its access immediately. This is like turning off its special badge so it cannot get into your system anymore. This helps contain any potential damage very quickly, which is pretty vital.
Another thing is having a way to update your devices remotely. If a security flaw is found in the software on your devices, you need to be able to push out a fix without having to physically visit every single one. This is crucial for patching problems and keeping your entire fleet safe over time. It is a bit like sending out a software update to your phone, but for your little IoT gadgets, as a matter of fact.
Also, having clear steps for investigating what happened is important. If an alarm goes off, you need to know who is responsible for looking into it, what information they need to gather, and what actions they should take. This helps you understand the problem and prevent it from happening again. It is about learning from incidents, basically, to make your system even stronger.
Putting It All Together for Remote IoT
Bringing all these pieces together to securely connect remote IoT devices to AWS VPCs means thinking about your entire setup as one big system. It is not just about one secure connection or one security feature; it is about how all the different parts work in harmony. From the little gadget out in the field to the powerful computers in the cloud, every step needs to be considered for safety. This holistic view is quite helpful, you know.
It starts with the device itself, making sure it is built with security in mind and has a unique way to identify itself. Then, it moves to the way the device talks, ensuring that all communications are scrambled and sent over private pathways, perhaps through a VPN or a direct link into your private cloud space. This creates a safe journey for your data, really.
Once the data reaches your AWS VPC, it enters a controlled environment where you decide exactly what can happen. You set up rules about who can access what, and you use tools to constantly watch for anything unusual. This layered approach, where security is built in at every stage, gives you a very strong defense against potential problems. It is like having multiple locks on your doors and windows, as a matter of fact.
And finally, it is about being prepared for when things do not go as planned. Having ways to quickly respond to security alerts, update devices remotely, and learn from any incidents helps you maintain a strong and resilient system over the long term. By combining these different aspects, you can confidently and securely connect remote IoT devices to your AWS VPC, knowing your information is well protected. It is a continuous effort, obviously, but a very worthwhile one.
AWS VPC Endpoints - Certification

AWS VPC Tutorial - Part I Introduction - StudyTrails

AWS VPC Peering - Certification